|
 |

Network Security
An insecure network is an invitation to compromise and abuse by internal and external security threats. While a completely invulnerable network cannot exist, there are some steps that can be taken to secure most existing networks. Comm-Tract can analyze your network and suggest ways to reduce the risk and enticement of attack.
After your network has been buttressed against possible immediate attacks, it’s time to develop a network security policy to ensure continuous protection. The point is that no organization can afford to be run without ground rules. Comm-Tract will turn your company’s trust in its people into rules that allow appropriate degrees of access to the information infrastructure. A solid network security policy will promote organization-wide patterns of behavior that will limit access to the network resources only to those originally intended.
After a well-thought strategy has been crafted, Comm-Tract can help with the implementation. This could also include ensuring your up-to-date conformance to the latest security norms and installation of security patches. You can remain confident in your organization’s ability to keep up with security threats while keeping your network connected to the outside world. With our Network Support Services you protect your investment in information resources and maintain the peace of mind necessary to perform your real job.
Basic Services Include . . .
HIPAAcheck
HIPAAcheck is a packaged solution providing the end user an action plan to start on the road towards HIPAA compliance, including a security gap analysis and vulnerability assessment. HIPAAcheck security assessments are designed to help healthcare organizations maintain confidentiality, integrity, and availability of their data systems.
HIPAAcheck Overview
SECUREcheck
SECUREcheck is a packaged solution for high-level internal and external network security assessment. Through the SECUREcheck process, the Pro Shop experts thoroughly scan and inspect the customer’s network to find and report known security vulnerabilities. SECUREcheck Overview
SECUREcheck Sales Slick (click file/save as to save document)
NETcheck
NETcheck offers a network assessment of a customer’s existing network. NETcheck determines current operating parameters and provides recommendations for improving performance and planning for future growth.
NETcheck Overview
NETcheck Sales Slick (click file/save as to save document)
HIPAAcheck
Do you need to be HIPAA compliant? HIPAA
Health Insurance Portability & Accountability Act
Requires the healthcare industry to protect the privacy of patient records. It's also designed to promote a national, uniform standard for the secure electronic transmission of patient-identifiable information.
Why Sell HIPAAcheck?Healthcare providers will need to address privacy protection and data security. Without it, they can face:
-
Non- Compliance Will Result in Civil and Criminal Penalties. Deadline: April 14th, 2003
-
Fines up to $25,000 for Multiple Violations in the Same Calendar Year.
-
Fines up to $250,000 And/or Imprisonment up to 10 Years for Knowing Misuse of Individually Identifiable Health Information.
Covered Entities Have Two Full Years to Comply With the Final Rule's Provisions.
HIPAAcheck Is a Gap Analysis and Security Vulnerability Assessment for Health Care Providers Data Networks.HIPAAcheck Consist of a Fixed Price Base Professional Service Package with Clearly Defined Deliverables.
Extended Services Are Available and Priced Separately.
What is a Security Vulnerability Assessment ?
...passively examining a network, and it’s assets, from an internal and external perspective, with the intent of discovering security voids or weaknesses.
These weaknesses could potentially be exploited, causing loss of data or resources to the client. The SECUREcheck Vulnerability Assessment will provide your customer with a snapshot of current security risks.
Eligible Devices for Assessment:
|
Eligible Servers
|
|
Eligible Servers
|
Windows
|
Apple
|
|
Solaris
|
Windows 2000
|
Macintosh
|
|
Linux
|
Windows NT
|
|
|
HP/UX
|
Windows 98
|
|
|
AIX
|
Windows 95
|
|
|
BSD
|
|
|
|
TRU64
|
|
|
|
|
Eligible Firewalls
|
|
Cisco PIX
|
|
Check Point Firewall-1
|
|
Axent Raptor
|
|
Sidewinder
|
|
Any IPCHAINS based firewall
|
|
|
Eligible VPN devices
|
|
Cisco VPN concentrators
|
|
Any PPTP device
|
|
What does HIPAAcheck Include?
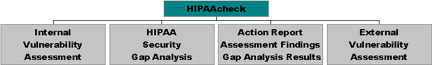
HIPAA Security Gap Analysis
-
Baseline inventory of systems, policy, procedure, practices and forms
-
Administrative, physical, and technical security review.
-
Review policies, procedures, process and practices relating to security and privacy.
-
Identify gaps between your customer’s current policies, procedures and systems to HIPAA requirements
Action Report Assessment Findings and Gap Analysis Results�
-
Determine impact of regulations on organization
-
Document differences between current IT policies, procedures, and systems to regulatory privacy requirements
-
Outline recommendations to bring IT policies, practices and systems into privacy compliance
-
Base plan to include – timeframe and actions
Assistance with electronic extension form filing
Common Features
External Vulnerability Assessment
-
Scan of Open Ports and Services on Inbound Permanent Connections
-
External Client Information Enumeration - Publicly Discovered Information About Internal Network Assets
-
Remote Access Policy Review
Internal Vulnerability Assessment
- Server Vulnerability Assessment
- Firewall Policy Review
- VPN Policy Review
- Router and Switch Open Port and Services Scan
Server Vulnerability Report
- Scan of open ports and services
- Operating system patch levels
- File system permissions
- Password policy review
- Antivirus protection
- Accounting / intrusion detection log analysis review
- Authentication methods
SECUREcheck:
Who Needs Security?
-
Highlights of the "2002 Computer Crime and Security Survey" Include:
90% of Respondents (Primarily Large Corporations and Government Agencies) Detected Computer Security Breaches Within the Last Twelve Months.
-
44% Percent (223 Respondents) Were Willing And/or Able to Quantify Their Financial Losses. These 223 Respondents Reported $455,848,000 in Financial Losses.
-
As in Previous Years, the Most Serious Financial Losses Occurred Through Theft of Proprietary Information (26 Respondents Reported $170,827,000) and Financial Fraud (25 Respondents Reported $115,753,000).
Consider the Following… Has your customer’s security policy stayed relevant to their current business model and infrastructure?
Do your customer’s have the expertise and resources to assess their network security requirements?
How long can they afford to be down due to a breach of security?
SECUREcheck will identify most aspects of vulnerability and expose the potential areas for policy development.
SECUREcheck Is a Security Vulnerability Assessment of a Private Data Network.
SECUREcheck Consists of a Fixed Price Base Professional Service Package with Clearly Defined Deliverables.
Extended Security Services Are Available and Priced Separately.
What is a Security Vulnerability Assessment?
...passively examining a network, and it’s assets, from an internal and external perspective, with the intent of discovering security voids or weaknesses.
These weaknesses could potentially be exploited, causing loss of data or resources to the client. The SECUREcheck Vulnerability Assessment will provide your customer with a snapshot of current security risks.
Eligible Devices for Assessment:
|
Eligible Servers
|
|
Eligible Servers
|
Windows
|
Apple
|
|
Solaris
|
Windows 2000
|
Macintosh
|
|
Linux
|
Windows NT
|
|
|
HP/UX
|
Windows 98
|
|
|
AIX
|
Windows 95
|
|
|
BSD
|
|
|
|
TRU64
|
|
|
|
|
Eligible Firewalls
|
|
Cisco PIX
|
|
Check Point Firewall-1
|
|
Axent Raptor
|
|
Sidewinder
|
|
Any IPCHAINS based firewall
|
|
|
Eligible VPN devices
|
|
Cisco VPN concentrators
|
|
Any PPTP device
|
|
What does HIPAAcheck Include?

Security Assessment Findings Report
External Assessment Deliverables:
-
Open ports/services with a description of the vulnerabilities of each.
-
Information discovered from publicly available sources.
-
Any weaknesses in the remote access policy.
Internal Assessment Deliverables:
-
Password weaknesses in the system. Also includes a recommendation on password policy.
-
Current backup policy and results of a recovery from the backup unit (if exists). This includes recommendations on backup policy.
-
Current authentication process for the system and recommendations for authentication.
-
Current IOS revision levels, open ports and general vulnerabilities for IOS and ports/services. This includes recommendations for tightening the security within routing and switching devices.
External Vulnerability Assessment
-
Scan of Open Ports and Services on Inbound Permanent Connections
-
External Client Information Enumeration - Publicly Discovered Information About Internal Network Assets
-
Remote Access Policy Review
Internal Vulnerability Assessment::
- Server Vulnerability Assessment
- Firewall Policy Review
- VPN Policy Review
- Router and Switch Open Port and Services Scan
Server Vulnerability Report:
- Scan of open ports and services
- Operating system patch levels
- File system permissions
- Password policy review
- Antivirus protection
- Accounting / intrusion detection log analysis review
- Authentication methods
SECUREcheck Extended Services
Additional Fee-based Remedial and Consulting Services Are Available. These Services May Be Purchased in Conjunction With or Independent of the Base Program. - Penetration Testing
- Enterprise Security Policy and Procedure Assessment
- Physical Security Assessment
- Web Site Vulnerability Assessment
- Custom Service
- On-demand Dial Service Assessment
- Application Vulnerability Assessment
NETcheck:
NETcheck Includes:
-
Examines and documents all network hardware
covering up to 100 network devices within a single
location.
-
Details network software inventory including network
device software versions.
-
Collects and reviews all Network equipment
configurations.
-
Complete documentation on Server network
connections.
-
Collects and documents all WAN circuit information.
-
Evaluates LAN device connectivity.
-
Surveys the Network layer protocol routing.
-
Review of current network security configuration and
Quality of Services (QoS), parameters.
-
Analyzes the current network management system
configuration.
-
Final review or assessment conducted by a Comm-Tract CCIE.
NETcheck Assessment Findings Report:
-
Diagrams of the current physical and logical network
topology.
-
Written analysis of current network status.
-
Documentation on current network device software-
configurations, hardware and software inventory and
network address plan.
-
Recommended upgrades including network hardware,
software, and management updates, WAN/LAN
bandwidth, and QOS implementations.
|